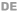Phishing e-Learning
Authentic e-learning against fake e-mails
Our best practice for phishing e-learning shows how companies can effectively sensitize their employees to dealing with fake emails. Instead of relying on standardized training courses, a didactic approach is presented that optimally combines theory and practice. First, the basics of phishing are explained: typical characteristics of phishing emails, tricks with links and URLs as well as the most important warning signals to look out for. This is followed by an interactive challenge in which learners have to check several authentically designed emails – adapted to the respective corporate environment. The aim is not only to decide whether it is a phishing email, but also to highlight the specific clues that expose the fraud. In this way, a practical and individual phishing awareness training course is created that shows how e-learning can be set up in the company to strengthen employee protection and cyber security in the long term.
Phishing e-learning is particularly effective when it is used specifically at the moment of need: for example, when an employee has actually fallen for a phishing email. The appropriate training can be assigned automatically via the learning management system – so individual learning takes place where it is needed, rather than according to the watering can principle.
Phishing remains the gateway to large companies
The problem
The risk of phishing attacks is particularly high in large companies with thousands of employees. Cyber criminals use deceptively genuine emails that are often overlooked in the hustle and bustle of everyday working life. Just one click on a manipulated link can be enough to reveal sensitive data or compromise entire systems. Standardized awareness measures often fall short here: they are too general, do not reach the relevant target groups and only create limited sustainable awareness. Our approach to phishing e-learning starts at precisely this point: with realistic, company-specific examples and practical exercises that pick up employees where the threat actually arises – in their daily e-mail traffic.

Individual phishing e-learning with practical relevance
The solution
Effective phishing e-learning for large companies is characterized by the fact that it does not follow a standard procedure, but reflects the real risks in the company. Instead of abstract examples, employees experience concrete situations that they could actually encounter in their day-to-day work. This noticeably increases awareness because the training has direct relevance. In addition, the learning format is designed to be flexible and scalable – whether for 500 or 50,000 employees. The approach is particularly effective if the training is not “worked through” once a year, but is used dynamically: for example, automatically when someone has fallen for a phishing email. This needs-based learning ensures that cyber security is not perceived as a compulsory exercise, but as concrete support in critical situations.
Dangerous links often go unnoticed
A central problem with phishing emails is that hyperlinks are not checked by most users. Many do not even realize that the true address of a link can be displayed simply by hovering over it with the mouse. It is precisely this brief glance that could make the difference between a safe click or entering a professionally faked phishing site.
But even if the URL is displayed, there is often a lack of knowledge about what to look out for when reading it: small deviations in the domain name, unusual endings or deliberately used special characters. Our approach to phishing e-learning therefore focuses precisely on this point: the training teaches how links can be safely checked and which patterns immediately look suspicious. In this way, employees learn not only to recognize suspicious hyperlinks, but also to clearly identify them – before any damage is done.
Recognizing phishing in everyday working life
Realistic e-mail scenarios
In the phishing e-learning course, participants work through a list of several emails – just like in real life when they open their inbox in the morning. Not all of the messages are dangerous, but many seem perfectly legitimate at first glance. Some come from internal departments, colleagues or known contacts, with familiar signatures, abbreviations or formatting. However, these inconspicuous emails conceal deliberately crafted phishing emails. The learners’ task is to identify them, explain exactly how the deception is recognizable and thus sharpen their own judgment.
To ensure that the training has maximum relevance, we develop the email scenarios individually to suit the company: with realistic senders, internal terms, department abbreviations or typical communication patterns. This creates a practical learning environment that not only sensitizes employees to theoretical risks, but also prepares them directly for the daily dangers in their own inboxes.
Recognizing phishing step by step
Realistic emails, clear decisions
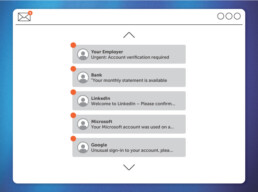
In the phishing e-learning course, participants see a deceptively real email that is modeled on the corporate environment – with matching senders, signatures and familiar wording. The task is to critically examine this message and decide whether it is phishing or not. In the process, a crucial aspect is trained that is often overlooked in practice: how to deal with hyperlinks. Before learners can even evaluate the email, they have to move their mouse over the link in order to display the actual URL. This is precisely how the “gap” is closed: many employees did not previously know how to check links reliably.
The exercise is structured in two stages: First, a decision is made as to whether it is phishing. This is followed by the second task, in which the learners have to explain specifically why the email is clearly a phishing message – for example due to suspicious URL structures, unusual domain endings or conspicuous sender details. This approach not only attracts attention, but also anchors the knowledge in the long term because it has to be applied immediately.

Traceable measurement of phishing detection
Clear evaluation of the results
At the end of the phishing e-learning course, each learner receives a detailed evaluation of their own decisions. All emails that were checked during the training are listed again – including the question of whether they were correctly classified as phishing or harmless. It is particularly important to check not only whether the right decision was made, but also whether the decisive clues were recognized and named. Only if the typical characteristics such as manipulated links, suspicious domains or conspicuous sender details have actually been identified is the task considered to have been completed.
This personal feedback is particularly helpful for the learners: they recognize exactly where they are already acting confidently and where there are still uncertainties. This gives them a clear picture of which details can be easily overlooked in everyday life – and where a phishing email might still deceive them. This transparency not only raises awareness, but also gives every employee concrete starting points to improve their awareness step by step and confidently fend off phishing attacks in future.
Recognize phishing before it is clicked.

Interview with Günther Veit
Why did you publish a best practice on phishing e-learning? What was the trigger?
We see at many large companies that phishing is still one of the biggest cyber risks – and yet awareness measures are often too superficial. Traditional e-learning courses or information videos may raise awareness, but they remain too general and therefore ineffective. Especially when it comes to phishing, this is not enough: employees must learn to recognize suspicious emails in their own context. That’s why we wanted to show what a practical concept looks like that can be applied directly in day-to-day business. We need to activate employees, especially in times of AI, when it is becoming even more difficult to check or recognize emails or voice phishing.
What does the approach look like in concrete terms?
The e-learning starts in a deliberately realistic way: learners receive a list of different emails – some are safe, others are clearly phishing. Just like in a real inbox, it is not immediately clear what is safe and what is not. Each email is examined individually and links have to be actively checked by hovering over them with the mouse. In this way, we train a crucial point that many employees were previously unaware of: that the true URL is hidden behind it. It is then important not only to say whether it is phishing, but also to explain how this can be recognized.
So the focus is on active action?
Exactly. Our aim was to turn passive information into an active decision-making situation. Only when employees check, decide and give reasons themselves will what they have learned really stick. That’s why we rely on authentic emails with real signatures, internal abbreviations or department names. This creates a scenario that feels absolutely realistic – and therefore significantly increases attention.
Is there another element that was particularly important to you?
Yes, the needs-based use. Phishing e-learning is most effective when it is used automatically when an incident has actually occurred – for example, when someone has clicked on a fake email. The appropriate training can then be assigned immediately via the learning management system. This makes the approach sustainable because learning takes place where there is a need – and not according to the scattergun principle.
In conclusion: What is special about this best practice for you?
It shows how to turn an abstract risk into tangible, interactive training. Employees experience phishing as they encounter it in their everyday lives – and learn to recognize dangers on their own. For me, the special thing is that we don’t focus on fear, but on confidence. Once you have been trained to check links and recognize suspicious patterns, you will automatically apply this in real working life. This is exactly what makes this best practice so valuable.
Online cybersecurity training – necessary and meaningful
Cybersecurity training online is not only possible, but more effective than expected - if…
Cybersecurity training online: What training should really achieve
A modern online cybersecurity training must do more than just warn. How e-learning…
e-Learning IT security: Why standard courses do not protect
e-Learning IT Security: How customized e-Learnings build awareness and real protection…
Online cybersecurity course for managers: responsibility starts at the top
Managers need customized online cybersecurity courses - for real responsibility and…
Online cybersecurity course: Why awareness alone is not enough
Online cybersecurity course: Strategic guidance for cybersecurity training. Why awareness…
IT security online course: these 5 mistakes to avoid
IT security online course: These mistakes should be avoided during development in order…
Cybersecurity online training with storytelling for real awareness
Cybersecurity online training with storytelling creates real awareness - why HR and…
Cybersecurity online course as a well thought-out curriculum
Curriculum-based cybersecurity online course concept: customized, adaptive content,…
Information security training as e-learning: protection for companies
Discover how customized information security training via e-learning works for large…